Understanding the nuances of network protection mechanisms is vital for maintaining a secure and efficient IT infrastructure. Loop Guard is a prominent feature used in network design to enhance the reliability and integrity of the spanning tree protocol (STP) environment. This article delves into the technical workings of Loop Guard, focusing on its interaction with Bridge Protocol Data Units (BPDUs) and how these interactions help safeguard networks from potential loop issues.
What is Loop Guard and Why is it Important?
Loop Guard is an advanced feature used in networking to prevent alternate or root ports from becoming designated ports due to a failure in BPDU transmission. This feature is critical in network environments where layer 2 switching is prevalent and the potential for loops is significant. By understanding the role Loop Guard plays, administrators can ensure higher network uptime and reduced service disruptions.
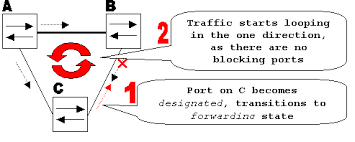
At its core, Loop Guard provides a safeguard mechanism that keeps track of BPDUs. If BPDUs are not received on a non-designated port and it starts to transition into the forwarding state, Loop Guard intervenes by putting the port into a loop-inconsistent state temporarily. This state prevents the transmission of user data until BPDUs are received again, thus maintaining the network's loop-free topology.
How Loop Guard Interacts with BPDU Transmission
The effectiveness of Loop Guard hinges on its interaction with BPDU transmissions. BPDUs are essential for the Spanning Tree Protocol (STP) as they carry information necessary for the root bridge election and subsequent configuration of the network's topology. Loop Guard fundamentally monitors the receipt of these BPDUs on all non-designated ports.
When enabled, Loop Guard checks continuously for the presence of BPDUs. If a port configured with Loop Guard stops receiving BPDUs for a certain duration—the Max Age timer plus the Forward Delay timer—it transitions the port into a loop-inconsistent state. This precaution ensures that in case of unidirectional link failures or improper configurations where BPDUs are obstructed or lost, the network does not fall prey to devastating broadcast storms or loops.
The Importance of Proper Configuration
For Loop Guard to function correctly, it must be configured properly across all switches within the network. Misconfiguration can lead to unintended behaviors, such as unnecessary traffic delays or even network outages. Therefore, a thorough understanding of network design principles, particularly relating to layer 2 topologies, is crucial.
Implementing Loop Guard involves understanding the detailed dynamics of your network's topology and how BPDUs are transmitted across it. As part of maintaining an optimal network design, it is beneficial to study foundational courses on layer 2 network design, which provide insights into effectively leveraging features like Loop Guard.
Moreover, administrators must also ensure that all network devices are compatible with Loop Guard and are running firmware that supports this feature. Regular updates and checks are necessary to avoid any discrepancies in BPDU transmission which might disable Loop Guard unintentionally.
Case Studies and Practical Implementations of Loop Guard
Examining specific case studies where Loop Guard has been implemented can provide deeper insights into its practical benefits and challenges. In large enterprise networks, where the risk of loops is higher due to complex configurations, Loop Guard plays a pivotal role in maintaining stability and preventing network downtime.
In one notable example, a major financial institution faced intermittent network failures traced back to unidirectional fiber link issues causing a cessation of BPDU transmissions. By implementing Loop Guard, the institution was able to detect and put the affected ports into a loop-inconsistent state before any looping issues could propagate, thus markedly reducing network downtime.
This case underscores the importance of proactive monitoring and configuration of Loop Guard in environments where network integrity is critical to business operations. It also highlights the necessity for ongoing training and awareness among network administrators to effectively utilize such security features.
Technical Deep Dive: Loop Guard Mechanism
Under the hood, the mechanism by which Loop Guard operates is governed heavily by the STP standards. STP works to ensure there is a single active path between network devices, preventing loops. When Loop Guard is enabled on a port, it starts in a Listening state and progresses to the Learning state after the Forward Delay timer expires, provided it continues to receive BPDUs.
If during this transition, BPDUs are lost and the port does not receive any for the duration defined by the Max Age plus Forward Delay timer, Loop Guard will trigger, moving the port into a loop-inconsistent State. This state is maintained until BPDUs are detected again, ensuring that partial network failures do not escalate into total network collapses.
To delve into the coding and configuration specifics, network administrators need to adjust STP settings carefully. Commands such as spanning-tree guard loop are used within interface configuration modes on switches to enable Loop Guard on specific ports. Detailed logging and monitoring are also essential to review the effectiveness of these settings and make necessary adjustments based on network behavior.
Lastly, troubleshooting Loop Guard requires meticulous attention to detail, particularly in deciphering STP transitions and understanding the implications of BPDU losses. Network simulation tools and detailed logs can aid significantly in diagnosing issues related to incorrect Loop Guard configurations or operational failures.
Conclusion: Maximizing Network Security through Loop Guard
In conclusion, Loop Guard is an instrumental feature in modern network environments, offering a critical safeguard against potential loop problems that could disrupt network operations. Through rigorous monitoring of BPDU transmissions, Loop Guard ensures that ports remain in a loop-inconsistent state until stability is verified, thus upholding network integrity.
Effective implementation and management of Loop Work are essential, as seen in various enterprise-level case studies. Proper configuration, routine monitoring, and continued education on network security best practices are indispensable in leveraging this feature to its full potential. As networks grow in complexity and scale, the role of advanced protocols and security mechanisms like Loop Guard will only become more crucial to ensuring seamless, uninterrupted network services.
Therefore, embracing comprehensive strategies that incorporate advanced tools like Loop Guard is necessary for any network-focused organization aiming at maintaining high levels of system uptime and security.


